
While working with AEM, sometimes we have requirements to call third-party APIs/Services. Configurations related to these APIs/Services like username, passwords, client id/secrets, API keys are usually stored in a code repository in the form of OSGi configuration. This sensitive information should be stored encrypted rather than plain-text format.
This is possible through the OOTB AEM Crypto Support bundle. This bundle provides services for encrypting and decrypting the confidential/secured data through system-wide keys (hmac and master files).
What are the Features of Crypto Support?
- Decryption happens at runtime.
- No one can decrypt the data through the UI. There’s no UI to decrypt the encrypted data. So, the information remains secure.
What are hmac/master keys?
- Encryption/decryption happens through keys (hmac and master files).
- These keys get generated during the first startup of AEM instance.
- In older versions of AEM (< 6.3), these files are stored under /etc/key but recent AEM versions have these files on the file system under crx-quickstart.
- These keys are unique for every AEM instance.
How to encrypt data using Crypto Support?
In order to encrypt a string, follow the below steps:
- Navigate to /system/console/crypto. The console looks like below:
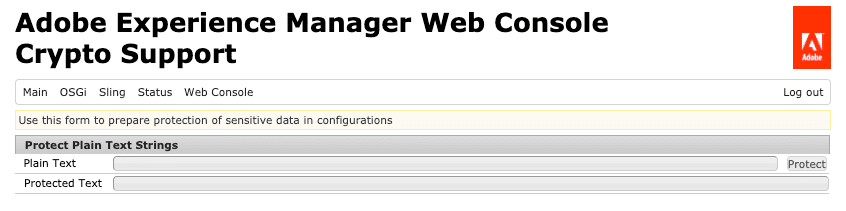
- Enter the plain-text string in the “Plain Text” field and click on “Protect”.
- An alphanumeric value will get generated in “Protected Text” field.
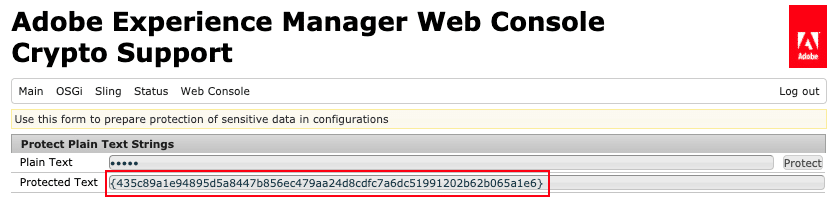
- Copy above alphanumeric value including curly brackets. For e.g. {435c89a1e94895d5a8447b856ec479aa24d8cdfc7a6dc51991202b62b065a1e6}
- Go to code base and put the above value in your OSGi config like below
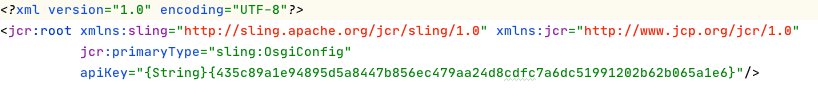
Note:
- Clicking on “Protect” again, will generate a new alphanumeric value. So, just click once and copy the alphanumeric value and put it in the code base.
- The encrypted value generated for the same plain-text string will differ from one AEM instance to another instance because keys are unique to each instance. We will talk about how to sync keys between the environments in our next blog.
How to decrypt data using Crypto Support:
@Reference
private CryptoSupport cryptoSupport;
public String getDecryptedValue(final String encryptedText) {
return cryptoSupport.isProtected(encryptedText)
? cryptoSupport.unprotect(encryptedText)
: encryptedText;
}
Note: For encrypted data, which is stored in OSGi configuration, we don’t need to call “unprotect” method explicitly as you see above. AEM has a Configuration Plugin to decrypt OSGi configuration properties. This plugin automatically decrypts and returns the plain-text string.
Get In Touch
Driving business growth by transforming challenges into opportunities with innovative, tailored solutions that deliver measurable results.

